Mar 4, 2020
Giving people the ability to pay only for what they use, as they need it, can lift millions of people across Africa out of poverty and make prosperity possible. A white paper from Mastercard titled “Pay on Demand: The Digital Path to Financial Inclusion”,...

Mar 3, 2020
The percentage of South African organisations who have experienced economic crime has significantly declined in 2020, returning to levels last seen in 2011, with the rate of reported economic crime has dropped 17 percentage points from 77% in 2018 to 60% this year....
Mar 2, 2020
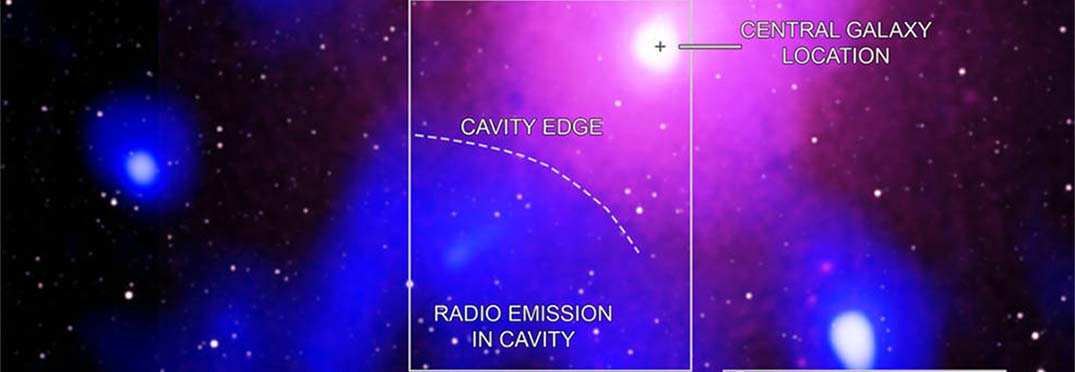
The biggest explosion ever seen in the universe so far has been spotted: the record-breaking eruption came from a black hole in a distant galaxy cluster hundreds of millions of light years away. “In some ways, this blast is similar to how the eruption of Mount...

Feb 28, 2020
Kathy Gibson is at the PwC post-budget briefing in Sandton – Finance Minister Tito Mboweni has promised to tackle government spending, and put the ball firmly back into the private sector’s court to make their own contribution to economic recovery by...

Feb 27, 2020
Shipments of traditional PCs (a combination of desktops, notebooks, and workstations) in EMEA is expected to total 72,2-million in 2020, a 1% year on year (YoY) decline. The remaining Windows 10 transitions will continue to drive demand in the commercial space, but...

Feb 26, 2020
Mobile malware detected in South Africa within 2019 saw a decrease in the number of attacked users compared to 2018. According to Kaspersky researchers, the overall number of users attacked fell from almost 20 000 to around 12 700. This, however, is different from the...